29th January 2026
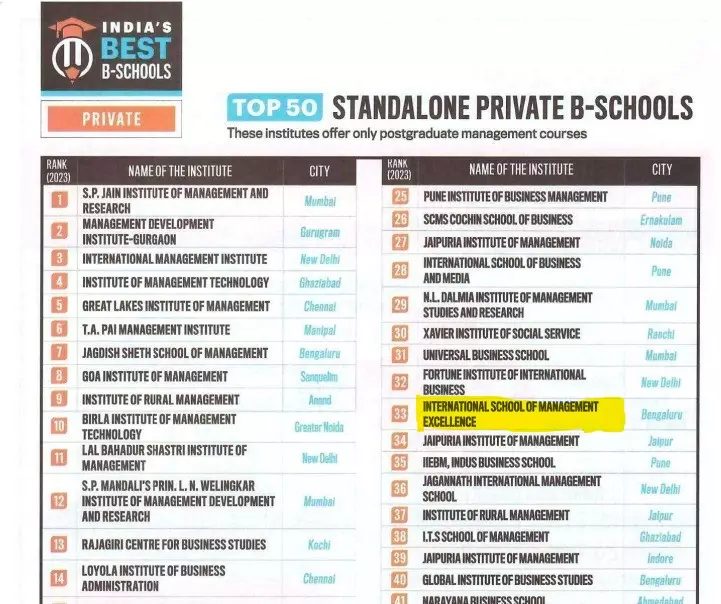
Management Excellence (ISME-Bangalore)
Course Relevance: Global business Analytics course for working professionals, Data Analytics, Design thinking and AI for a PGDM students and Problem-solving technique, for BCA and MCA.
Teaching Note:
- Understand key cybersecurity threats faced by professionals and educators
- Identify human and technical vulnerabilities in digital environments
- Apply basic cybersecurity practices to protect academic and professional data
- Recognize the importance of institutional policies and shared responsibility
- Develop awareness of cyber resilience and incident response strategies
Academic Concepts:
- Cybersecurity fundamentals and protection of digital systems
- Information Security Triad (Confidentiality, Integrity, Availability – CIA Model)
- Human factors and cyber awareness in information security
- Phishing and social engineering attacks
- Identity and Access Management (IAM)
- Multi-Factor Authentication (MFA)
- Data privacy and data protection principles
Introduction:
Dr. Asha Raman had always been proud of how seamlessly technology had blended into her work as an educator. As the Head of the School of Business at Blue River University, she encouraged her faculty to experiment with digital platforms—learning management systems, cloud-based classrooms, virtual labs, and even AI-assisted learning tools. For years, these changes created a lively environment where students could collaborate beyond physical boundaries and faculty could access information instantly.
But early one Monday morning, she received a message that froze her in place:
“Your institutional account has been locked due to suspicious activity.”
Following the link provided, she found a chilling notification:
“All your department’s academic files have been encrypted. Pay 12 Bitcoin within 72 hours or lose access permanently.”
A ransomware attack.
Thousands of assignment submissions, research files, student information, confidential reports, and faculty documents—everything had been locked. It felt surreal. Blue River University had always believed it had “basic cybersecurity measures” in place, but clearly, something had slipped through. And that “something” was now threatening years of academic data.
The Events Leading Up to the Attack
Two days before the breach, Assistant Professor Ravi Mehta received an email that looked like it came from the university’s IT support team. The message claimed that new security patches needed to be installed urgently. The email used the university logo, signature fonts, and even the IT helpdesk format. But the sender’s address was slightly off—it ended with “.tech-support.com” instead of “.edu.”
Ravi was in a rush to prepare for his lecture. Without thinking much, he clicked on the link and downloaded the “patch.” Within seconds, his screen flashed, then returned to normal. He dismissed it as a technical glitch.
Unfortunately, the malware embedded in that link silently activated, spreading through the faculty network, identifying shared folders, and encrypting files over the weekend when no one was monitoring the system. By the time the IT team detected the anomaly Monday morning, the damage was done.
The Immediate Consequences
Blue River University went into panic mode:
- Classes were disrupted because the LMS was partially locked.
- Student anxiety skyrocketed, especially final-year students whose projects and internship reports were inaccessible.
- Faculty members had lost lecture content, research data, and administrative files.
- The university’s reputation was threatened—parents, students, and partners demanded answers.
The administration called an emergency meeting. Cybersecurity experts were brought in to assess the situation. The ransom was too high, and the attackers’ identity was unknown. Paying did not guarantee data recovery.
The cyber experts explained that this type of attack—known as a phishing-triggered ransomware infiltration—had become increasingly common among educational institutions.
The university had, unintentionally, become a case study of the digital risks faced by professionals and educators today.
The Root of the Problem
The cybersecurity audit revealed five major vulnerabilities:
1. Human Error & Low Cyber Awareness
The phishing email fooled Ravi because he lacked training in identifying cyber threats. Many faculty members admitted they rarely checked sender addresses or verified links.
2. Weak Password Practices
Several accounts shared passwords across devices and platforms, making it easy for the attack to spread.
3. Outdated Systems
The university’s servers were running outdated security patches, making them more susceptible.
4. Lack of Zero-Trust Policy
Users were trusted by default once inside the network. The malware moved freely between folders without detection.
5. No Encrypted Backup
Backups existed but were directly connected to the main network. Once the ransomware spread, it encrypted the backups too.
The experts concluded that the attack could have been prevented with basic cybersecurity hygiene.
A Turning Point: The Cyber Restoration Project
Realizing that immediate recovery wasn’t enough, Dr.Asha launched the Cyber Restoration and Resilience Initiative (CRRI). It had two main goals:
- Recover and restore critical data.
- Build a long-term cybersecurity culture across the institution.
The initiative involved faculty, students, IT teams, and external cybersecurity consultants.
How Professionals and Educators Worked Together
1. Implementing Multi-Factor Authentication (MFA)
Every account—faculty, student, admin—was moved to MFA. Even if a password leaked, unauthorized login became impossible.
Dr. Asha used a simple analogy during the awareness session:
“Passwords are like house keys. MFA is like having an alarm, a guard, and a camera in addition.”
2. Mandatory Cyber Hygiene Workshops
Training modules included:
- Recognizing phishing attempts
- Checking URLs and sender IDs
- Safely storing academic files
- Responsible use of public Wi-Fi
- Spotting signs of malware
Ravi, ashamed of the role he unknowingly played, volunteered to share his experience as a cautionary story. It had a powerful impact—educators became more attentive to digital behaviour.
3. Data Encryption for All Digital Files
Every sensitive document—including student information—was encrypted.
Only authorized personnel had access keys.
4. Establishing a “Zero-Trust” Framework
No device or user was trusted automatically—even if connected internally. Every login, file transfer, and system access had to be verified.
5. Isolated and Encrypted Backups
Backups were moved offline, with regular testing and versioning.
Cyber experts emphasized: “A backup is only useful if it survives a cyber-attack.”
6. Creating an Incident Response Team
A cross-functional team was established to monitor suspicious activities and respond immediately. Students studying cybersecurity were also given roles, turning the crisis into a practical learning opportunity.
7. Redesigning Digital Classrooms
Security features were added to the LMS:
- Restricted upload permissions
- Regular password refresh
- AI-based threat scans
8. Promoting a Culture of Shared Responsibility
For the first time, cybersecurity was discussed not as a technical issue but as a collective responsibility.
The Road to Recovery
Restoring the encrypted data took nearly three weeks. Luckily, the cyber experts managed to decrypt 80% of the files using advanced recovery tools, avoiding the need to pay the ransom. The remaining losses forced the university to think deeply about the fragility of digital dependence.
During this period, students and faculty had to improvise:
- Professors recreated lecture materials.
- Students resubmitted assignments when possible.
- Administrative staff shifted to offline documentation temporarily.
What surprised Dr. Asha was how supportive the academic community became. Instead of blame, there was cooperation. Instead of fear, there was determination to rebuild.
A New Digital Culture Emerges
Six months after the attack, BlueRiver University successfully became one of the most cyber-resilient institutions in the region.
Key positive transformations:
- Faculty were educated about cyber risks with regular refresher courses.
- Students created a “Cyber Champions Club” to advocate safe digital practices.
- The IT team implemented 24/7 network monitoring.
- Annual cybersecurity drills became mandatory.
- Policies for handling academic data became stricter and more systematic.
What had begun as a devastating breach evolved into a transformative journey.
Key Lessons for Professionals and Educators
The case of BlueRiver University highlights essential principles relevant to every digital-age professional:
1. Cybersecurity is not optional.
Digital tools bring convenience, but they also carry risk. Every educator, manager, or student must treat cybersecurity as part of daily responsibility.
2. Human error is the biggest vulnerability.
Technology can be secured, but careless clicks can break the entire system.
3. Regular training is crucial.
Cyber threats evolve. So must awareness.
4. Backups must be redundant and secure.
One backup is not enough. And no backup should be online 24/7.
5. Institutions need a clear cyber response strategy.
Without it, valuable hours are lost in confusion during a breach.
6. Cyber resilience is a collective effort.
Security improves only when everyone works together.
Conclusion
The BlueRiver University case demonstrates how easily a single careless click can compromise an entire institution. Yet it also shows the power of collaboration, awareness, and strategic action. In the digital age, professionals and educators carry immense responsibility—not only to use technology but also to protect the data entrusted to them.
Cybersecurity is no longer a technical requirement.
It is a fundamental skill.
A mindset.
A culture.
The digital world will only become more complex. But with informed, vigilant, and empowered individuals, institutions can thrive securely—even amid evolving cyber threats.
References:
- Stallings, W. (2020). Cryptography and Network Security: Principles and Practice. Pearson Education.
- Whitman, M. E., & Mattord, H. J. (2021). Principles of Information Security. Cengage Learning.
- Anderson, R. (2020). Security Engineering: A Guide to Building Dependable Distributed Systems. Wiley.
- NIST (National Institute of Standards and Technology). (2018). Framework for Improving Critical Infrastructure Cybersecurity. NIST Special Publication.
- ISO/IEC 27001:2013. Information Security Management Systems – Requirements. International Organization for Standardization.
Discussion Questions:
- What role did human error play in the cyber incident?
- How can educators and students reduce phishing risks?
- Should institutions pay ransom in cyberattacks? Why or why not?
- How does cybersecurity differ from traditional IT security?
- Why is cybersecurity a shared responsibility?